TL;DR / At-a-Glance Summary
What is BYOD?
A policy allowing employees to use personal devices (smartphones, tablets, laptops) for work activities. A formal BYOD policy defines which devices and employees are covered, what software must be installed, and how data is secured.
Why BYOD?
Organizations adopt BYOD to save device procurement costs, increase employee satisfaction and productivity, and leverage the latest personal technology. A 100‑person company can save ~$50 k per year by offloading device purchases.
Key challenges:
BYOD increases security risks, complicates IT support and introduces privacy concerns. Unchecked devices may run outdated software or lack strong passwords.
Best practices:
Establish a written BYOD policy detailing scope, approved devices, required security software, acceptable use, privacy rights, and protocols for lost devices. Use strong authentication, enforce mobile device management (MDM), adopt least‑privilege access and train employees.
Spenza’s role:
We provide operator‑neutral connectivity and unlimited mobile plans, enabling affordable BYOD for enterprises and MVNOs. Our platform helps unlock device‑locked phones, supports eSIM onboarding, and reduces BYOD operational complexity.
For detailed guidance, read our sub-articles on BYOD Planning, BYOD Policies, and MVNO Locked-Phone Challenge & BYOD.
Jump to
- Introduction
- What Is BYOD?
- Benefits of BYOD
- Challenges of BYOD
- Implementation Best Practices
- Spenza’s BYOD Offering
- Conclusion: Transforming BYOD into a Competitive Advantage
- FAQs

Introduction
The way employees access work resources has transformed. Instead of being issued a company-owned laptop or phone, many professionals now bring their own device (BYOD) to work. BYOD simply means an employee uses their personal smartphone, tablet, or laptop to access corporate email, apps, or data. This approach delivers convenience and flexibility but also introduces security, privacy, and support challenges. With mobile workforces and remote/hybrid teams growing, it’s no longer a niche practice — nearly 90% of global IT departments now allow some form of BYOD.
This article serves as your central, authoritative resource for understanding and implementing a successful BYOD program. Whether you are an IT decision-maker, an enterprise mobility lead, or an MVNO operator, you will find the context, guidance, and best practices necessary to navigate the opportunities and challenges of BYOD. We will explore the core tenets of BYOD, from policy creation and security to the specific challenges faced by MVNOs in a world of locked devices.
Furthermore, we will illustrate how Spenza’s solutions can empower your organization to embrace BYOD with confidence — ensuring a secure, scalable, and successful implementation.
What is bring your own device (BYOD)?
“Bring Your Own Device” refers to an organization’s practice of permitting employees to access work email, applications and data using their own personal devices. A BYOD policy outlines the parameters for this arrangement: which devices are permitted, which employees can participate, what security software (such as MDM or antivirus) must be installed, and what constitutes acceptable use. It also clarifies privacy rights and ownership of data, describes how to handle lost or stolen devices (e.g., remote wipe), and defines off‑boarding procedures when an employee leaves.
This approach has gained significant traction over the past decade, with approximately 67% of employees using personal devices for work, according to recent industry surveys.
The shift toward BYOD has accelerated due to several factors:
- Remote Work Revolution: The global pandemic normalized remote work, making BYOD essential for business continuity
- Digital Transformation: Organizations need flexible mobility solutions to support modern workflows
- Employee Expectations: Today’s workforce expects the convenience of using familiar devices
- Cost Considerations: Reducing capital expenditure on devices offers significant budget advantages
BYOD vs. COPE vs. CYOD
- BYOD (Bring Your Own Device): Employees supply their own devices and are responsible for maintenance and upgrades. The company enforces security policies via MDM or containerization.
- COPE (Corporate‑Owned, Personally Enabled): The organization owns the device but allows limited personal use. This gives IT greater control but increases procurement costs.
- CYOD (Choose Your Own Device): Employees select from a pre‑approved list of devices that the company purchases. This balances control and user preference.
Understanding these models helps IT leaders choose the right approach. Many organizations deploy a hybrid BYOD/COPE strategy, offering corporate devices for users who need strict compliance while allowing BYOD for others.
Benefits of BYOD
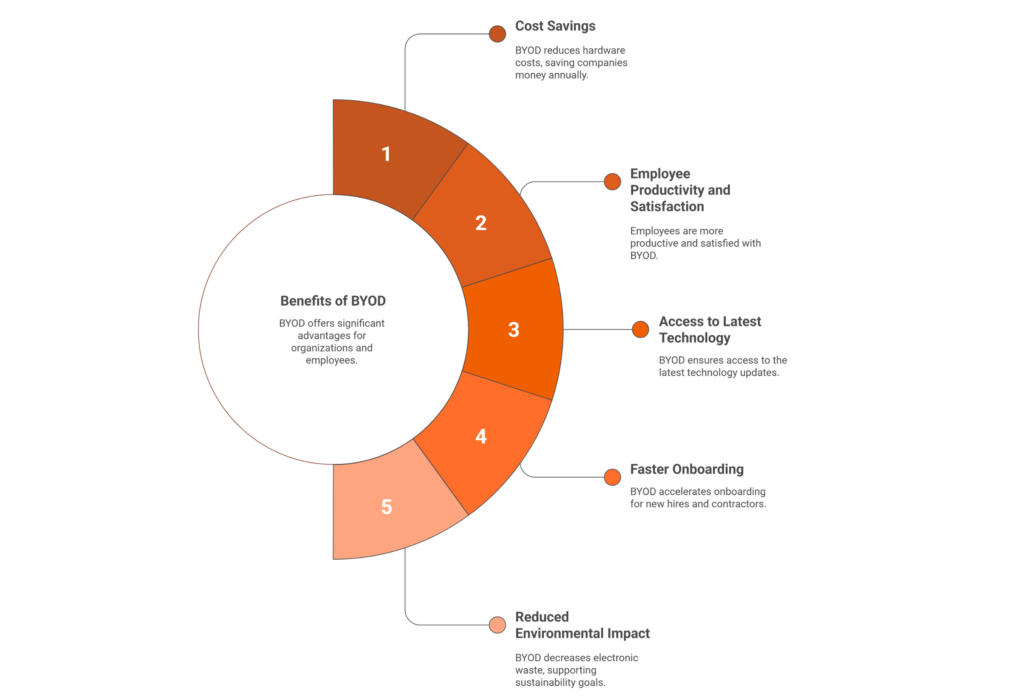
- Cost Savings: BYOD avoids the need to purchase and maintain hardware for every employee. Okta notes that company‑issued smartphones and laptops are expensive, whereas allowing personal devices reduces capital expenditure. Spenza’s BYOD planning article estimates that a 100‑person company saves approximately $300 – 500 per person per year by eliminating device stipends.
- Employee Productivity and Satisfaction: Employees already know how to use their own devices, reducing training time and boosting efficiency. About half of employees report their personal devices are better than work‑issued ones. Employees also appreciate having a single device for work and personal use.
- Access to Latest Technology: Personal devices are often newer and more frequently updated than corporate hardware. Employees naturally upgrade their phones and tablets, ensuring the organization benefits from modern technology.
- Faster Onboarding: BYOD accelerates employee onboarding because new hires can start working immediately with their own devices. This is especially valuable for contractors and remote workers.
- Reduced Environmental Impact: Fewer corporate devices means less electronic waste. BYOD supports sustainability goals.
Challenges of BYOD
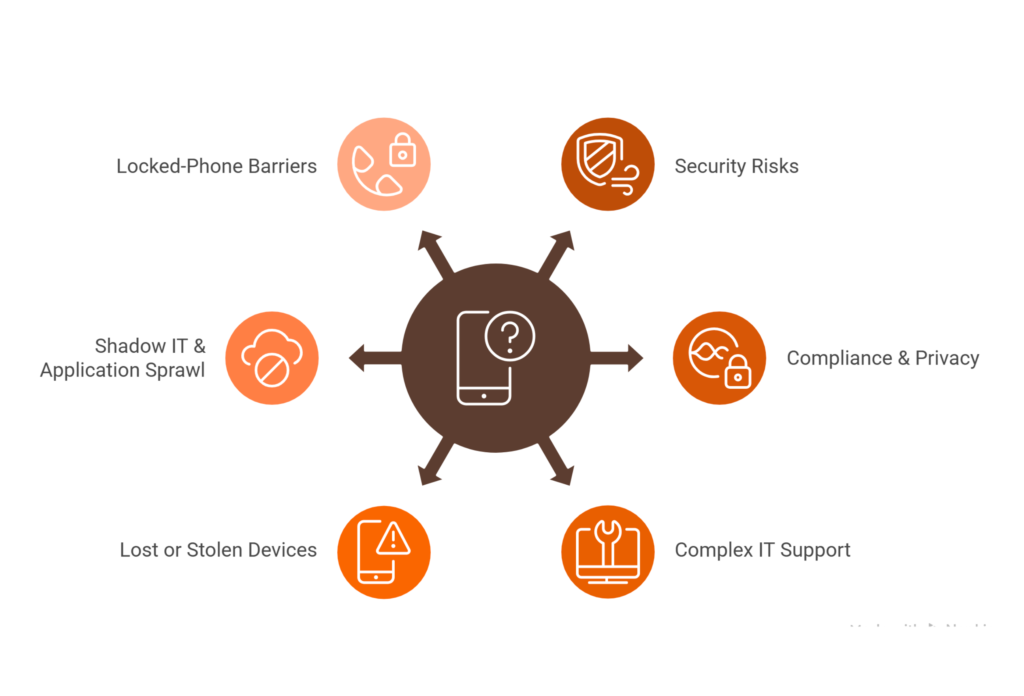
- Security Risks: Personal devices may run outdated operating systems, lack strong passwords or be infected with malware. Okta cautions that additional devices and employees with less oversight open the corporate network to vulnerabilities. ConnectWise warns that human error and weak passwords are the top cyber threats in a BYOD environment.
- Compliance & Privacy: Mixing personal and corporate data creates privacy dilemmas. A BYOD policy must explain how company data will be monitored and what privacy rights employees retain. Regulations such as GDPR, HIPAA or banking rules may require strict separation of personal and work data.
- Complex IT Support: IT teams must support diverse device types and operating systems. This diversity increases troubleshooting time and may require specialized tools or training.
- Lost or Stolen Devices: Personal devices are more likely to be lost or stolen outside the workplace. Without clear protocols, sensitive corporate data could be exposed. A strong BYOD policy should mandate immediate reporting and remote wipe capabilities.
- Shadow IT & Application Sprawl: Employees may install unauthorized apps or bypass corporate tools, leading to data leakage and compliance gaps. Continuous monitoring and auditing are essential.
- Locked‑Phone Barriers (for MVNOs): For mobile virtual network operators (MVNOs), BYOD is critical for customer acquisition. However, major carriers have tightened device locks, preventing locked phones from activating on competitor networks and causing up to 85% of potential customers to be ineligible for BYOD. This increases marketing costs and support burden.
BYOD Implementation Best Practices
Successfully adopting BYOD requires deliberate planning. The following guidelines synthesise recommendations from experts:
- Develop a Formal BYOD Policy: Document the scope (who and what devices are included), device requirements (supported operating systems, required MDM/antivirus), acceptable use rules, data ownership and privacy rights, protocols for lost or stolen devices, and exit procedures. Publish the policy and obtain employee acknowledgement.
- Use Strong Authentication: Enforce complex passwords or passphrases and require multi‑factor authentication (MFA) for accessing corporate resources. Combine MFA with biometric authentication where possible.
- Implement Mobile Device Management (MDM) or Mobile Application Management (MAM): Use MDM software to install security agents, enforce encryption, separate personal and work data, and enable remote wipe. For privacy‑sensitive environments, consider containerization or secure enclaves to segregate corporate data.
- Adopt Least‑Privilege and Zero‑Trust Principles: Provide access only to the resources an employee needs. Implement role‑based access controls, privileged access management (PAM) and continuous monitoring. Assume devices are untrusted until proven safe.
- Educate and Train Users: Regularly train employees on secure practices such as avoiding public Wi‑Fi, recognizing phishing attempts, and reporting lost devices immediately. Contractor or partner training is equally important.
- Define Incident Response Processes: Outline how to handle device loss, theft or compromise. Include procedures for revoking access, remote wiping and conducting post‑incident reviews.
- Monitor and Audit Devices: Continuously monitor device health, OS versions and compliance with policies. Audit logs for suspicious activity and enforce periodic checks.
- Balance Privacy and Control: Be transparent about what data IT will collect (e.g., device status, installed software) and what remains private. Separate personal and corporate data where possible to respect employee privacy.
- Plan for Off‑Boarding: Define steps to remove company data when an employee leaves. This may involve instructing the employee to uninstall corporate apps, returning SIM cards or revoking credentials.
For a deeper, step‑by‑step blueprint, read our BYOD Planning guide. It explains how BYOD policies evolved from early concerns about device control to modern acceptance and highlights cost‑saving calculations and tips for selecting carriers.
Spenza’s BYOD Offering
Spenza is more than a connectivity provider — we’re your partner in enabling BYOD securely and cost‑effectively. Here’s how we support your BYOD journey:
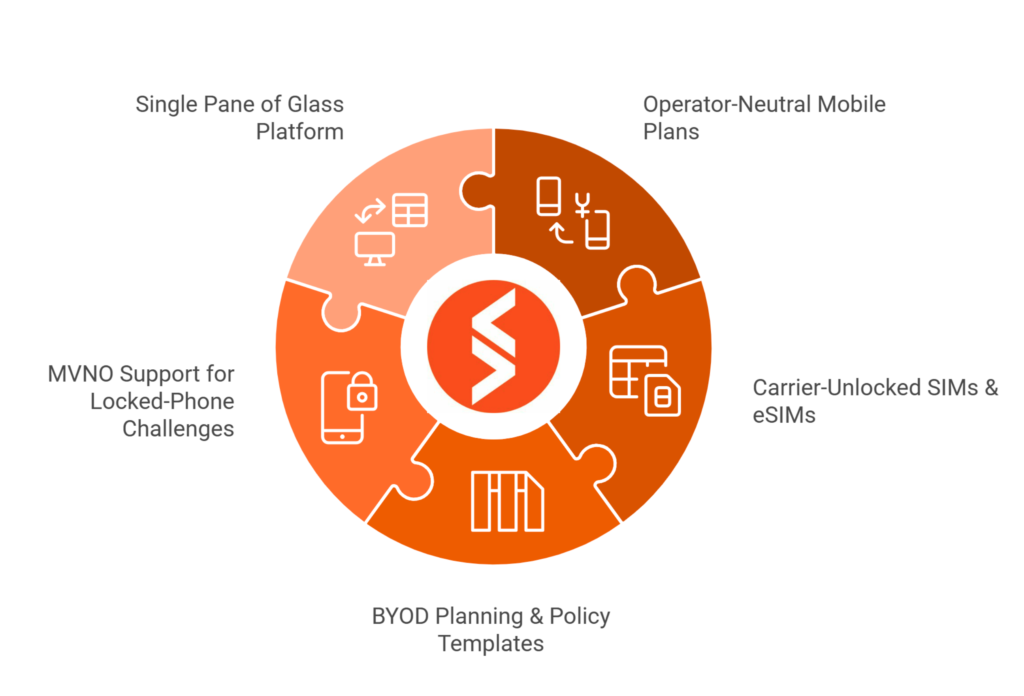
- Operator‑Neutral Mobile Plans: We offer unlimited mobile plans from all three major U.S. carriers starting at very low prices, roughly 50% cheaper than typical corporate plans. Customers can choose the network that works best for them without being locked into a single carrier.
- Carrier‑Unlocked SIMs & eSIMs: Our SIMs can be used in any unlocked device and we support eSIM activation for digital onboarding. This eliminates the friction and delays of shipping physical SIM cards.
- BYOD Planning & Policy Templates: Through our BYOD Planning and BYOD Policies articles, we provide policy templates and cost‑savings calculators. For example, a 100‑employee business spends ~$50–100 k annually on corporate devices; BYOD combined with our plan can slash those expenses.
- MVNO Support for Locked‑Phone Challenges: Our MVNO Locked‑Phone Challenge guide explains how tightened carrier locks jeopardize BYOD growth for MVNOs. We help MVNOs verify IMEI compatibility, pivot marketing to “Bring Your Unlocked Phone,” diversify by selling affordable devices, and leverage eSIM for instant activation.
- Single Pane of Glass Platform: We offer a cross‑carrier MVNA + MVNE platform enabling B2B/B2B2C operations for MVNOs. This single interface reduces complexity, tracks activations, manages billing and simplifies BYOD adoption.
Case Examples / Scenarios
Scenario 1: Mid‑Size Enterprise Adopts BYOD
A 200‑employee technology firm spending $900 per employee per year on corporate smartphones decides to adopt BYOD. Using Spenza’s policy template and cost calculator, they issue a stipend for mobile plans but stop purchasing devices. With employees using their personal phones and Spenza’s unlimited plan, the firm saves approximately $400 per user per year — a total of $100 k in annual savings.
The IT team uses MDM to separate corporate and personal data and deploys MFA for secure access. Employee satisfaction rises due to device choice, and onboarding times drop from days to hours.
Security incidents remain low because the firm follows the best practices outlined above.
Scenario 2: MVNO Navigates Locked‑Phone Challenge
An MVNO that built its business around BYOD suddenly sees device activations rejected after major carriers tighten their IMEI locking policies. Roughly 90% of BYOD attempts are now blocked. By consulting Spenza’s Locked‑Phone Challenge guide, the MVNO implements pre‑signup IMEI checks, educates customers about unlocking rules (e.g., T‑Mobile postpaid devices unlock after 40 days and prepaid after 365 days), and pivots marketing to emphasize “Bring Your Unlocked Phone.”
They introduce refurbished device sales and eSIM onboarding to reduce activation friction. Partnering with Spenza’s platform allows them to manage multiple carriers and maintain growth despite tighter locks.
Conclusion: Transforming BYOD from Challenge to Competitive Advantage
Navigating the BYOD landscape is no longer optional — it’s a strategic imperative for modern enterprises seeking agility, cost-efficiency, and a satisfied workforce. As we’ve explored, the path to a successful BYOD program requires balancing significant benefits with complex challenges around security, management, and compliance.
The key takeaway is clear: a successful BYOD strategy is not just about allowing personal devices — it’s about implementing a robust framework of policies, technologies, and support that empowers employees while protecting enterprise assets. This is where Spenza excels. Our comprehensive BYOD management platform is designed to address the full spectrum of your needs — from overcoming unique MVNO challenges to streamlining policy creation and ensuring seamless implementation.
By partnering with Spenza, you transform BYOD from a potential liability into a powerful competitive advantage. You gain the peace of mind that comes with enterprise-grade security, the efficiency of unified management, and the flexibility to adapt to the evolving mobile landscape.
The future of work is mobile, flexible, and user-centric. Your BYOD program should be too.
FAQs
BYOD lets employees use their own devices for work. CYOD (Choose Your Own Device) supplies a list of approved devices that the company purchases. COPE (Corporate‑Owned, Personally Enabled) gives employees a company‑owned device that permits some personal use.
Small to mid‑sized businesses looking to reduce hardware costs and improve flexibility often benefit the most. However, large enterprises and MVNOs can also deploy BYOD with proper policies and MDM. In fact, nearly 90 % of IT departments worldwide support some form of BYOD
Implementation timelines vary based on organization size and complexity, but most programs can be launched in 1-3 months with proper planning.
Yes, our platform is designed to integrate seamlessly with existing enterprise systems, including identity management, security tools, and productivity applications.
Spenza offers unlimited plans from major carriers starting at very low prices, roughly half the cost of traditional corporate plans. We also provide unlocked SIMs/eSIMs and guidance on BYOD policies and planning.
Ready to modernize your BYOD program? Request a free demo to see how Spenza can slash costs, simplify connectivity and secure your mobile workforce.