TL;DR / At-a-Glance Summary
What Is APN
An Access Point Name (APN) tells a cellular device how and where to connect, whether to the public internet or a private network.
How APNs Affect IoT
APNs determine routing, IP assignment, and security policies for connected devices, making them foundational in IoT communications.
Public vs. Private APNs
Public APNs are shared and simple, suitable for low-risk use cases; private APNs are isolated, secure, and essential for enterprise deployments.
Why Private APNs Matter
Private APNs improve security through traffic isolation, controlled access, and regulatory compliance for sensitive or large-scale IoT systems.
Centralized APN Management with Spenza
Spenza streamlines APN configuration across carriers and regions, offering unified management, security controls, and reduced operational complexity.
Understanding What an APN Is
If you are building or managing connected devices, you have probably come across the term APN in your SIM settings or IoT dashboard.
But what is APN, and why does it matter so much in connected deployments?
In simple terms, an access point name determines how a device connects to the internet through a mobile network. It tells the network where the data should go and how it should be handled.
Think of it like a shipping label on a package.
When you send a parcel, the courier does not guess the destination. The label clearly defines:
- Where the package must go
- Which route should it take
- How it should be processed
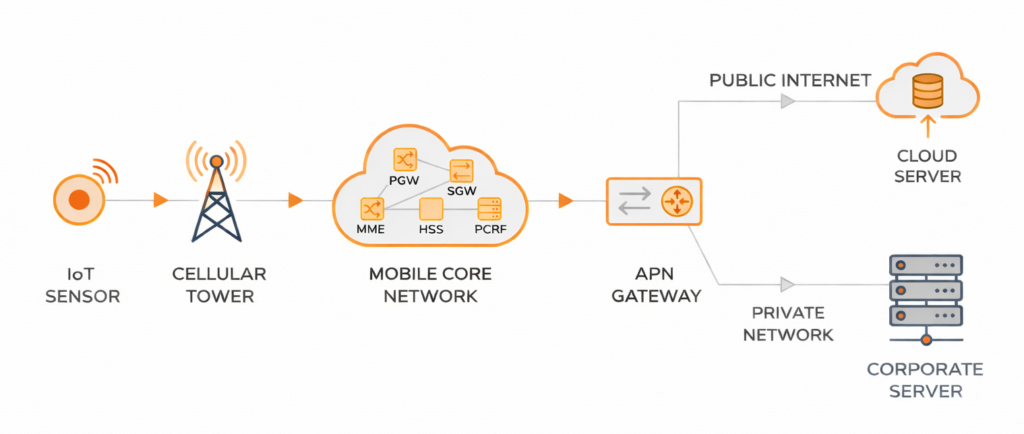
In the same way, when an IoT device sends data over cellular, the network needs instructions. The access point name acts as that label. It defines how data packets travel from the device to your cloud server or enterprise system.
Whether you’re managing a fleet of connected vehicles, deploying smart meters across a city, or running industrial sensors in a remote warehouse, APNs are quietly doing some of the heaviest lifting behind the scenes.
According to GSMA Intelligence, global IoT connections are expected to exceed 24 billion devices by 2030, more than doubling current deployments.
As device counts grow into the tens of thousands per organization, foundational elements like APN configuration and IoT deployments move from technical settings to infrastructure decisions.
By the end of this blog, you’ll not only understand what an APN is, but also why it matters enormously for enterprise IoT deployments, how it works, and what decisions you’ll need to make around it.
Let’s decode it, step by step.
What Does an APN Actually Do?
APN stands for Access Point Name. It is the network setting that tells a cellular device how to establish a data connection through a mobile carrier, whether to the public internet or a private network.
More technically, an APN is a short string of text configured on a device or SIM card that tells the carrier’s network a few important things:
- What kind of network connection to establish (internet, private network, etc)
- What IP address to assign to the device
- What security credentials are required, if any
- What traffic routing rules apply
An APN string typically looks something like this: internet.carrier.net or company.private.apn
Breaking It Down Simply
Imagine a warehouse logistics system.
- The mobile network is the shipping company
- The IoT device is the package
- The cloud server is the destination
- The APN is the shipping label with routing instructions
Without the correct label, the package sits in the warehouse.
Without the correct access point name, the device connects to the network but cannot send data properly.
This is why understanding what an APN is is foundational for APN IoT deployments.
How APNs Work in IoT
Now that we understand what an APN is, let’s look at what actually happens under the hood when an IoT device uses one.
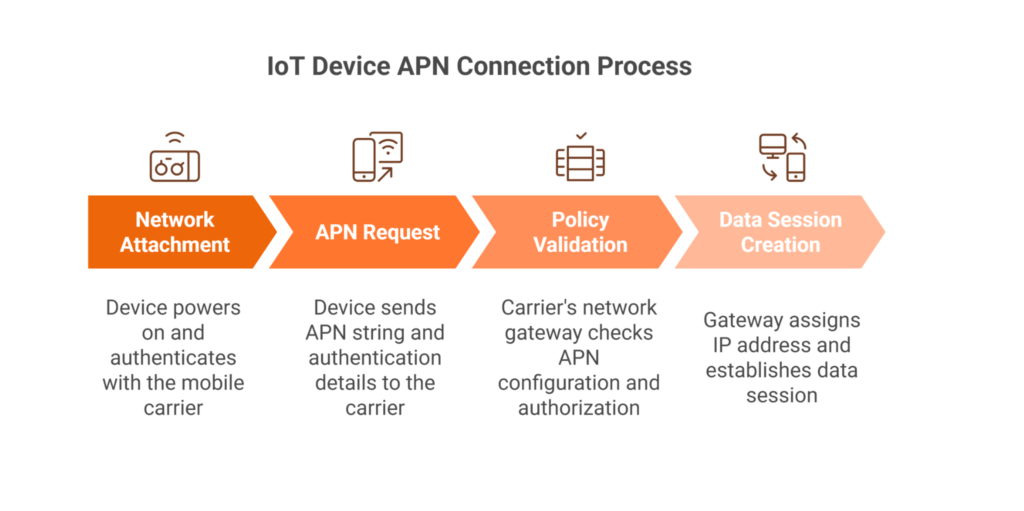
Here’s the step-by-step process when an IoT device connects using an APN:
Step 1: Network Attachment
The device powers on, and the SIM card activates. The SIM authenticates with the mobile carrier. The device joins the cellular network.
Step 2: APN Request
The device sends its APN string to the carrier’s network, along with any required authentication details. It essentially says:
“I want to open a data session using this access point name.”
Step 3: Policy Validation
The carrier’s network gateway receives this request and checks the APN configuration to understand:
- Is this SIM authorized for this APN?
- Should this device receive a public IP or a private IP?
- Are there traffic restrictions?
Step 4: Data Session Creation
Based on the APN settings, the gateway assigns an IP address, routes traffic to the appropriate destination (whether that’s the public internet, a private server, or a corporate network), and establishes a data session.
Now the data flows between the IoT device and its destination through this established path. This could be sensor readings, commands, telemetry updates, or firmware packages.
Real-Life Use Case: Smart Vending Machines
Consider a company deploying 20,000 connected vending machines across multiple cities.
Each machine:
- Reports inventory levels
- Sends payment data
- Receives pricing updates
If all devices use a public access point name, traffic travels over the public internet; if they use a private APN, traffic routes directly to the company’s secure backend system.
The APN configuration IoT setup determines how securely and efficiently the data travels. In large deployments, that routing decision has operational and security implications.
What makes this especially powerful in IoT is that devices on the same carrier network can use different APNs. A fleet management company might run all its GPS units on a private APN, fully isolated from the public internet, while a consumer smartwatch on that same carrier uses a public APN. The network is the same, but the routing rules and security boundaries are completely different.
That separation is not just convenient. It is essential. And it leads to one of the most important decisions in any IoT deployment.
Public vs. Private APNs
Once you understand how APNs work, the next natural question is: which type should you use? There are two main categories, public APNs and private APNs, and the difference between them goes far beyond just a name.
Public APN:
A public APN is the standard access point name provided by carriers to connect devices to the public internet. It is shared across all customers on that network. When you insert a SIM into a phone, and it connects automatically, that is a public APN at work.
Private APN:
A private APN is a dedicated access point name configured for a specific organization. Instead of routing traffic over the public internet, it sends data through a secure, isolated path directly to the company’s systems. It acts like a private lane reserved only for that organization’s devices.
Here’s a side-by-side look at how the two compare:
| Feature | Public APN | Private APN |
|---|---|---|
| Access | Shared with all carrier customers | Dedicated to a specific organization |
| IP Addressing | Dynamic, shared public IPs | Static, dedicated IPs (often private ranges) |
| Security | Standard internet-level security | High — isolated traffic, VPN support |
| Cost | Lower or included in carrier plans | Higher costs — setup and management fees apply |
| Traffic Routing | Routes to the public internet | Routes to private network or corporate backend |
| Use Case | Consumer devices, low-risk applications | Enterprise IoT, healthcare, finance, critical infrastructure |
| Visibility | Data flows through shared infrastructure | Data stays within a controlled environment |
| Setup Complexity | Simple, usually pre-configured by the carrier | Complex, requires carrier coordination |
For many IoT projects, especially early-stage or low-sensitivity ones, a public APN is perfectly fine. But as deployments grow in scale or handle more sensitive data, the limitations of a public APN become very apparent, very quickly.
Why Private APNs Matter for Enterprise IoT
A public APN is like a shared highway. Traffic moves freely, but it is mixed with everyone else on the network.
A private APN is like a secured lane reserved for your organization, where only authorized devices are allowed to communicate.
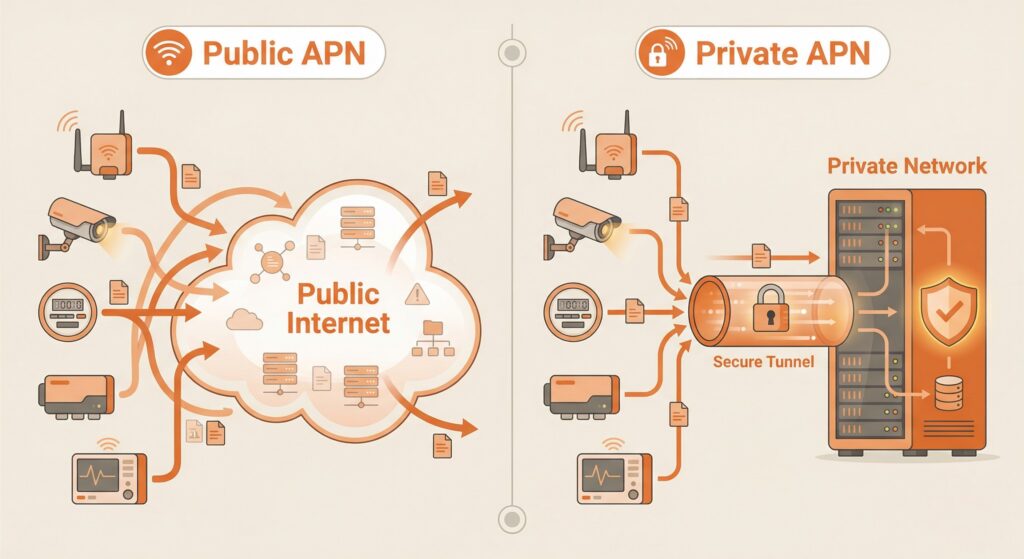
For small deployments, public access point name settings may be enough. For enterprise IoT, private APN becomes strategic.
Enterprises manage:
- Thousands of IoT devices
- Sensitive operational data
- Distributed global assets
Private APNs are not a luxury for enterprises across healthcare, logistics, utilities, and manufacturing. They are often necessary and are a foundational requirement.
For companies exploring branded connectivity or embedded mobile services, private APN architecture also plays a central role in launching an MVNO and controlling end-to-end traffic routing.
Here’s why.
Security Benefits
When IoT devices operate through a private APN, they function within a logically isolated network segment. This means they are not exposed to the same risks as devices sitting on the open internet. A few of the key security advantages include:
- Devices are not reachable from the public internet unless explicitly configured to be
- Authentication is required before any connection is established
- Traffic can be routed through encrypted tunnels, typically via IPsec or VPN, between devices and backend servers
- Access controls can be applied at a granular level, so specific devices only communicate with specific servers
Example: Consider connected ATMs.
If those machines use public APN routing, they are technically reachable through public infrastructure.
With a private APN, traffic flows through a secure tunnel into the bank’s internal systems. External access is restricted. This is not theoretical risk mitigation. A single breach in financial infrastructure can lead to multimillion-dollar fraud losses, regulatory penalties, and severe damage to customer trust.
According to IBM’s Cost of a Data Breach Report, the average global data breach cost reached $4.88 million in 2024, with critical infrastructure sectors experiencing even higher losses.
This reinforces why private APN and traffic isolation are not optional in sensitive deployments.
Traffic Isolation
Beyond security, traffic isolation through a private APN delivers operational clarity and control. Traffic isolation means keeping your device communication separate from general internet traffic.
Public APN traffic shares network paths with millions of users. Private APN creates a logical separation. With a private APN in place, all device traffic flows through known, controlled endpoints. This makes monitoring straightforward.
If a device starts behaving abnormally, sending data to an unexpected server, for instance, it gets flagged immediately. Quality of Service rules can also be applied, ensuring that critical communications get bandwidth priority over less important traffic.
Example: Imagine a distribution center with:
- General delivery lanes for public shipments
- A secured loading dock reserved only for enterprise goods
Private APN functions like a secured dock. Only authorized traffic enters and exits.
For industries such as manufacturing, logistics, or energy, this isolation protects operational systems.
For industries facing strict data regulations, such as finance, utilities, and healthcare, traffic isolation also simplifies compliance. You can clearly demonstrate that sensitive data never left your controlled environment, which is exactly what regulators want to see.
Configuring APNs Across Carriers
Understanding what an APN does is one thing. Actually setting one up, especially across a global deployment with multiple carriers, is where things get more hands-on.
For public APNs, most carrier SIM cards come pre-configured. For IoT deployments, however, APN configuration usually needs to be handled more deliberately, either at the device level, the SIM level, or through a remote provisioning system.
The most common parameters you’ll encounter when configuring an APN include:
- APN Name: The gateway identifier string, such as iot.carrier.net
- APN Type: Defines the kind of traffic the APN handles, such as default data, MMS, or location services
- Username and Password: Required for APNs that use authentication protocols like PAP or CHAP
- Proxy and Port: Optional fields for routing through a specific server
- MCC and MNC: Mobile Country Code and Mobile Network Code, which identify the carrier
Each carrier may define its own access point name format. These differences often stem from how carriers structure their connectivity infrastructure, as explained in this MVNE vs MVNA vs MNO comparison.
Real-World Example: Smart Utility Meters
In global IoT deployments, devices often cross country borders and switch between carrier networks mid-journey. A utility company deploys smart electricity meters in three countries.
Each country uses a different carrier with different APN settings.
If APN configuration for IoT devices is handled manually:
- Provisioning becomes error-prone
- Troubleshooting becomes difficult
- Device rollout slows down
Centralized orchestration simplifies this by abstracting carrier differences. A well-configured multi-carrier SIM, paired with the correct APN settings, ensures seamless connectivity without requiring manual changes on the device.
Some modern IoT platforms support dynamic APN switching, where the system automatically selects the best APN for the current network environment.
APN Management at Scale
Configuring an APN for a few devices is simple. Doing it for 50,000 devices across 30 countries is not. At scale, APN management becomes an ongoing operational responsibility, not a one-time setup.
Enterprises working with multiple carriers must navigate different access point name formats, routing rules, IP assignment models, and private APN requirements. Managing APN configuration IoT across separate carrier portals creates fragmented workflows, inconsistent security policies, and limited visibility across global deployments.
At that scale, even minor misconfigurations can lead to outages, security exposure, and costly operational delays.
Spenza addresses these challenges by centralizing multi-carrier APN IoT management into a single operational layer. Instead of configuring access point name settings carrier by carrier, enterprises can define policies once and apply them consistently across networks.
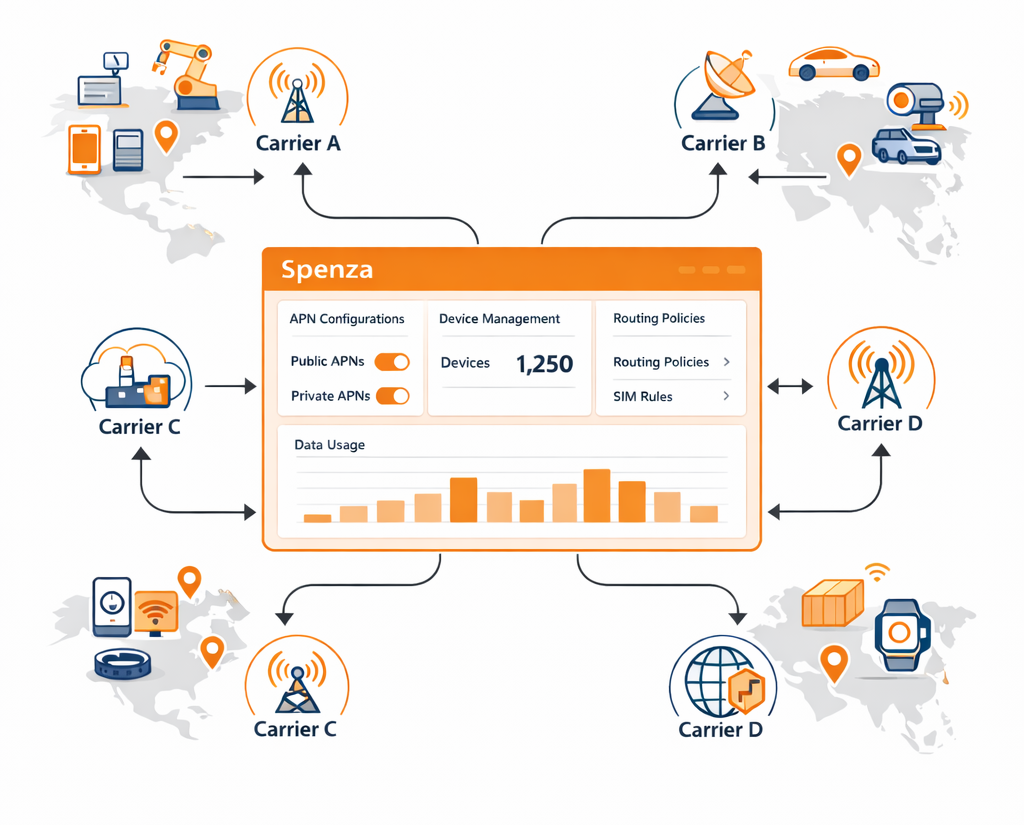
Organizations can:
- Configure public and private APN settings from one interface — Carrier-specific formats and provisioning workflows are abstracted, reducing manual configuration errors.
- Standardize routing and IP policies globally — Consistent traffic routing and IP allocation rules can be enforced across regions and carriers.
- Maintain traffic isolation and security controls at scale — Private APN environments can be provisioned with defined routing paths and controlled access policies.
- Provision and update APN configuration IoT settings in bulk — Changes can be applied across large SIM fleets without logging into multiple carrier systems.
- Monitor connectivity and session activity centrally — Teams gain unified visibility into device behavior and data sessions across carriers.
By consolidating APN management, organizations shift from fragmented carrier-level control to a structured, security-aligned connectivity architecture.
This shift aligns with the broader telecom-as-a-service model, where connectivity infrastructure is abstracted and centrally orchestrated rather than managed carrier by carrier.
Final Thoughts
Understanding APN architecture is fundamental to building reliable cellular connectivity. In APN IoT deployments, the access point name quietly determines how data flows, how securely it travels, and how well your infrastructure can scale. What appears to be a simple configuration setting often shapes the performance and resilience of your entire deployment.
For small projects, a public APN may work just fine. But as deployments grow across regions, carriers, and use cases, private APN and centralized APN configuration IoT strategies become critical architectural decisions. APNs are not just network settings. They are the routing foundation that supports secure, scalable connected operations. As IoT becomes a critical infrastructure, APN strategy becomes part of enterprise risk management.
FAQs
MVNOs often provide more flexible private APNs, multi-carrier support, and better management tools.
Explore how Spenza enables secure, multi-carrier APN IoT management from a single platform. Schedule your personalized demo today!